What is Encryption and Decryption?

As developers, there are going to be times when we need to be able to keep digital information secret from individuals who we don’t trust. Encryption gives us the ability to keep our secret information secret and allows us to keep our jobs if we work with sensitive information.
In this article, we’re going to go over what encryption is, why we need it, and discuss the major types.
What is Encryption/Decryption?
Encryption is the process of encoding information so only authorized parties can then decode (decryption) the information. This is done by converting the original information, also known as “plaintext”, into a form known as ciphertext.
When we’re working with electronic encryption, we generally use a key that is generated using a pseudo-random method. It is technically possible to decrypt the data if the attacker doesn’t possess the key but in reality, most encryption methods are so well designed that this is not easy to do as it requires a lot of computing power to brute force the key from the encrypted data.
There are two ways data can be encrypted “at rest,” when it is stored, or “in transit,” while it is being transmitted.
Why Do We Need Encryption
Encryption has a lot of benefits for both us and our end users.
Privacy is by and large the biggest benefit. By using encryption, we can be sure that no one can read data or communications except for individuals who should have access to the data. An example of privacy through encryption is something we use every day. SSL and TLS, the protocols that change our websites from HTTP to HTTPS, provide privacy so nobody intercepting the transmission between a client and a website can see the data transmitted between them.
The next benefit we gain from encryption is security. Encryption will help prevent data breaches of data. If a storage device is stolen or an S3 bucket is marked as public having that data encrypted will prevent random people from reading the information.
Encryption can also make sure that our data hasn’t been altered. We can make sure the data still has its integrity by verifying a signed digital signature of the data.
Encryption can provide authentication to our data. Public key encryption can be used to verify that the owner of a website is the one originating the data and not an un-trusted third party. Public key encryption can also be used to encrypt data so only the owner of the corresponding private key can decrypt the data which authenticates they are the ones who should have access.
Finally, encryption can provide regulatory compliance. Multiple compliance standards require encryption to be used throughout the data transfer and storage processes.
How Does Encryption/Decryption Work
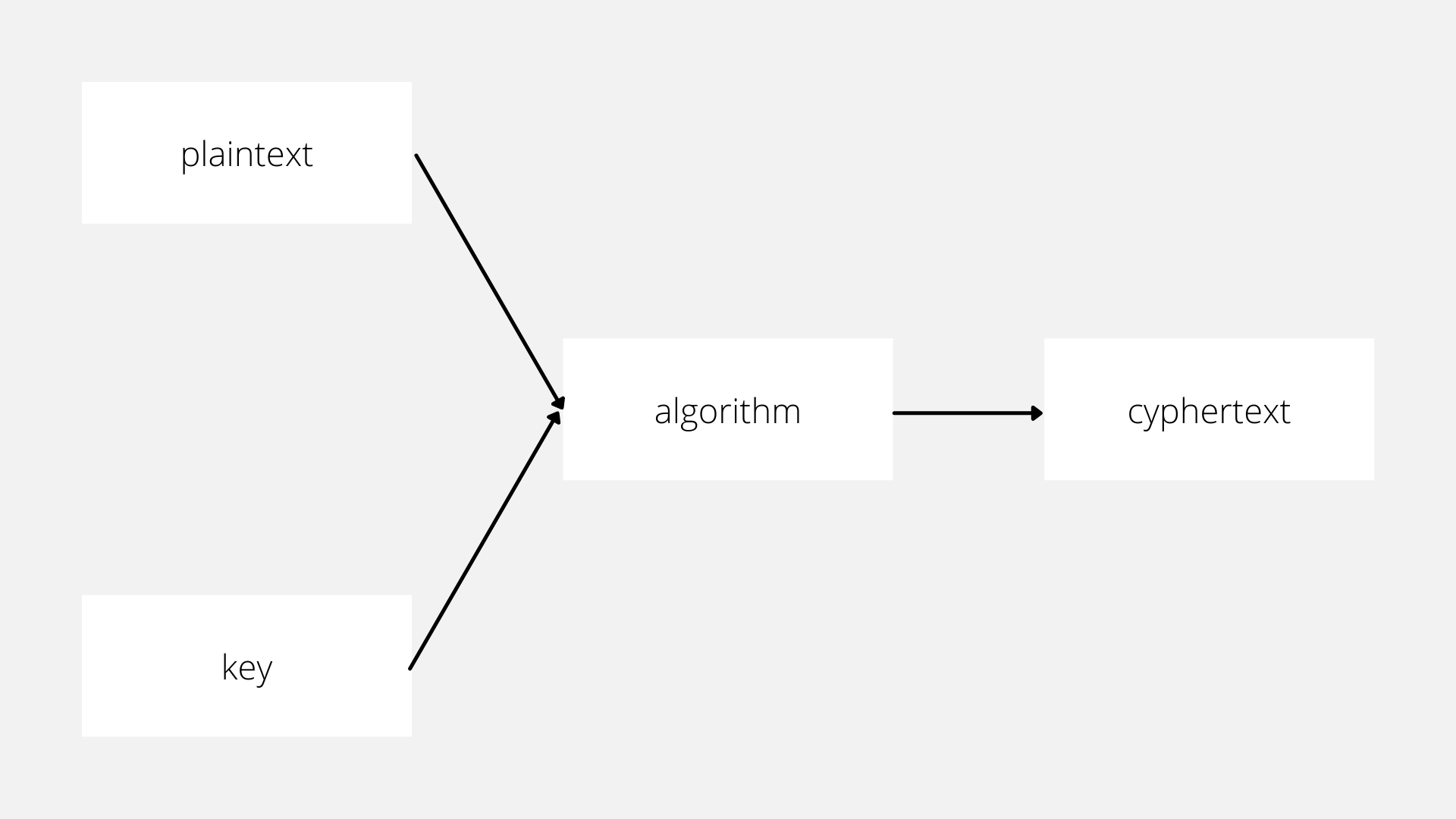
Encryption and decryption need two inputs to the system.
The first thing we need is the data to encrypt. We call this data plaintext and it can be anything. Credit card information and grandma’s secret cookie recipe are both valid data we might want to encrypt.
The second thing we need is a cryptographic key. A cryptographic key is a string of characters the encryption algorithm will use to alter the plaintext. It’s called a “key” because like a key we might secure our home with the key locks or encrypts our data and it can only be unlocked or decrypted when someone unlocks it using the correct key. Much like a physical key, we don’t want to be giving it out to anyone on the street and we’re only going to give it to people we truly trust.
After we have our plaintext and key we need to pick an algorithm that will perform the encrypting/decrypting. There are a lot of potential options for encryption algorithms like AES and Salsa208. When we first get started it’s going to be an acronym soup but don’t be overwhelmed.
When picking an encryption algorithm it’s important not to catch “not-invented-here syndrome” and attempt to write our own implementation of an encryption algorithm or even worse invent our own. Encryption algorithms are hard to understand and even harder to implement correctly and even professionals make mistakes.
After we take all these pieces and run the plaintext and the key through the algorithm we’ll get our output of ciphertext.
If the algorithm is designed correctly the ciphertext will look as though someone randomly picked bits of data.

There’s a famous example called the ECB Penguin that shows an encryption algorithm that doesn’t do this and is potentially insecure. The ECB Penguin took a picture of Tux the Penguin and ran it through the AES encryption. The output produced another image that while encrypted shows a very clear structure in relationship to the input.
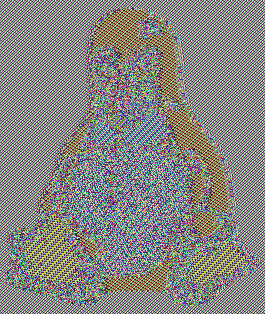
Ideally, the output should look like this.
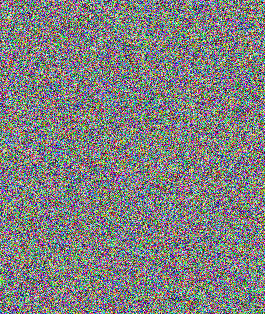
A Historical Context
It’s kind of interesting to look at the historical context for encryption.
In the information age, we use encryption every day when we browse the internet but for most of history, encryption was a manual process that was only employed by the military.
The most basic form of encryption is symbol replacement which replaced one character for another. The downside to this technique is that it is easy to brute force as there are only a set number of changes so we can perform an analysis of the frequency of each letter in the ciphertext and deduce the input text.
Another well-known example of historical encryption is the Enigma Machine. It was used by the Axis powers and contained a set of physical wheels that would rotate as the message was encrypted and decrypted. The wheels were reset to a different initial position every day so no two days would have the same initial positions making it difficult to crack. The Allies had to create a computer specifically to crack the Enigma’s encryption it was so powerful.
Encrypting in the Information Age
Encrypting and decrypting data in the information age is another beast entirely because computers can do more math much faster than any human. Except for maybe that kid from Mercury Rising.
When we discuss encryption strength we’re talking about the number of bits that are used in the key and the how hard it would be to break the encryption using brute force. Generally, the more bits in the key the stronger the encryption so we’ll get more strength from a 512 bit key than a 128 bit key. For example, DES originally used 56-bit keys but that only allowed for a possible key space of 2^56 (72,057,594,037,927,936) which can be brute forced using cloud computing in a reasonable amount of time. The minimum for modern encryption keys is upwards of 1024 bits which is impossible to brute force because the key space is so large (2^1024 = 179,769,313,486,231,590,772,930,519,078,902,473,361,797,697,894,230,657,273,430,081,157,732,675,805,500,963,132,708,477,322,407,536,021,120,113,879,871,393,357,658,789,768,814,416,622,492,847,430,639,474,124,377,767,893,424,865,485,276,302,219,601,246,094,119,453,082,952,085,005,768,838,150,682,342,462,881,473,913,110,540,827,237,163,350,510,684,586,298,239,947,245,938,479,716,304,835,356,329,624,224,137,216 possible keys!).
“Failures”
We talked about how it’s technically possible for attackers to break our encryption. There are only a couple of ways to do this. The most basic way is to brute force the encryption key used for the encryption. As commuting resources have gotten cheaper it’s possible to use something like https://crack.sh/ to break a DES key in less than a day. As we move to larger key sizes this becomes less and less likely. A 1024 bit key increases the keyspace so much it would be prohibitively expensive for any non-nation state to break the encryption and even then they would want to get to that data.
It’s also possible to find flaws in the encryption algorithm. This is less likely but it does occasionally happen.
The final attack to break encryption is an attack on the computers or individuals who possess the keys as KXCD 538 explains so well. It’s much easier to get a message someone is sending if an attacker installs a keylogger on the victim’s computer and is logging all their keystrokes or they just physically force them to give up their key.
What You Need To Know to Nail a Job Interview
- Encryption is the process of encoding information so only authorized parties can then decode the information
- Encryption provides:
- Privacy
- Security.
- Integrity
- Authentication
- Regulatory Compliance
Scott Keck-Warren
Scott is the Director of Technology at WeCare Connect where he strives to provide solutions for his customers needs. He's the father of two and can be found most weekends working on projects around the house with his loving partner.
Top Posts
- Working With Soft Deletes in Laravel (By Example)
- Fixing CMake was unable to find a build program corresponding to "Unix Makefiles"
- Upgrading to Laravel 8.x
- Get The Count of the Number of Users in an AD Group
- Multiple Vagrant VMs in One Vagrantfile
- Fixing the "this is larger than GitHub's recommended maximum file size of 50.00 MB" error
- Changing the Directory Vagrant Stores the VMs In
- Accepting Android SDK Licenses From The OSX Command Line
- Fixing the 'Target class [config] does not exist' Error
- Using Rectangle to Manage MacOS Windows