What is Symmetric and Asymmetric Encryption?

As developers, there are going to be times when we need to be able to keep digital information secret from individuals who we don’t trust. Encryption gives us the ability to keep our secret information secret and allows us to keep our jobs if we work with sensitive information.
In this article, we’re going to discuss the two types of encryption and go over the pros and cons of each.
Who Are Alice and Bob?
As we work through some examples we’re going to be referring to Alice and Bob to be the two people who are trying to have a secure conversation and are worried about a third person (Carol) listening in. They aren’t a specific Alice, Bob, or Carol.

Symmetric Encryption
When we’re discussing encryption there are two basic types. The first and more simple of the two is symmetric encryption.
In symmetric encryption algorithms, the same key that’s used to encrypt the plaintext is used to decrypt the ciphertext. This is great from a complexity standpoint but it presents some issues. The biggest being we need to have some way to send the key to all of the parties involved in the data exchange and each group of people in a conversation needs its own key.
Let’s see how this affects Alice and Bob.
To recap, Alice wants to send an encrypted message to Bob without Carol being able to see it. I want to believe it’s a recipe for the best chocolate cake ever made but you draw your own conclusions.

In a symmetric encryption process, Bob and Alice have had to meet in person to exchange the key they’ll be using (as that’s the only way to be sure nobody else copied it en route).
Alice then uses the key to encrypt her message.
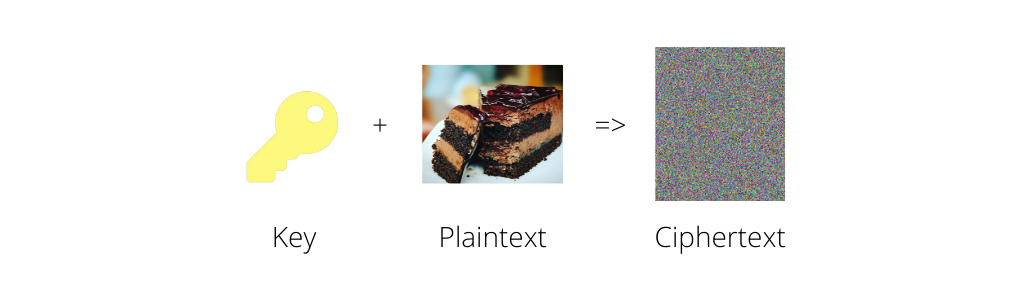
She can then safely send the ciphertext Bob who is then able to decrypt ciphertext to plaintext using the same key.
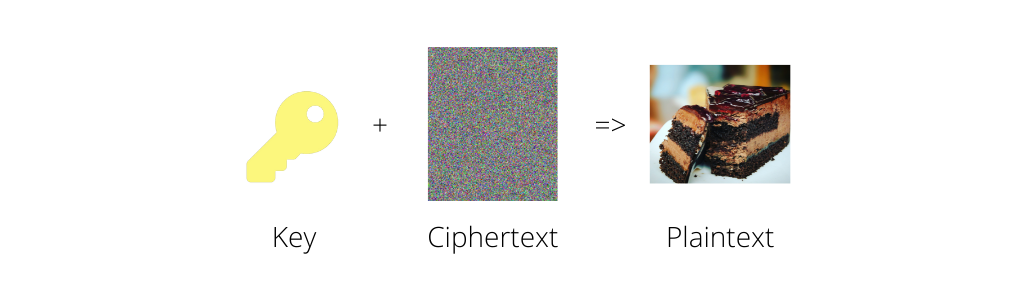
Other than the manual process of the key exchange it’s a fairly simple process.
Asymmetric encryption (Public/Private Key)
The second type of encryption is Asymmetric Encryption. This is also referred to as public-key or public/private key encryption and all three terms can be used interchangeably.
Using public-key cryptography each person sending a message has two keys. A public key that can be shared freely and a private key that must be guarded. Ideally, the private key would never leave a computer it was generated on so it stays super secure. The powerful part about public-key cryptography is that we can use both the public key or the private key to encrypt data but the only way to decrypt the data is to have the opposite key.
Let’s talk about what Alice and Bob need to do with public-key encryption to send each other their secret recipe.
Both Alice and Bob will email each other their public keys. This can be done through email because anyone can have a public key that’s why it’s a public key.
Now when Alice wants to send a message to Bob she will encrypt the message using her private key and Bob’s public key. This makes it so only someone in possession of Bob’s private key and Alice’s public key can decrypt the message.
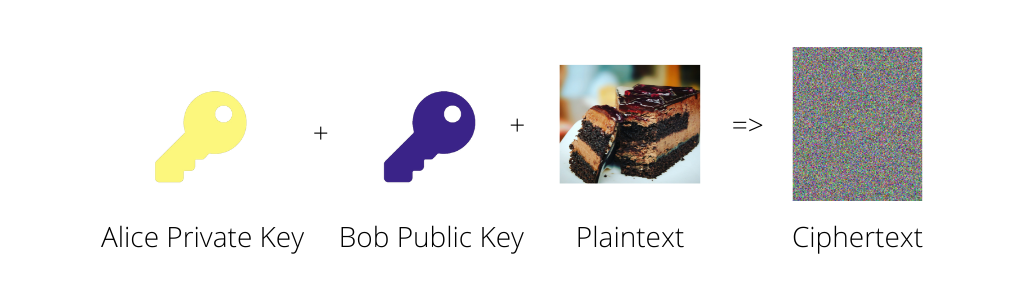
Then she sends the ciphertext to Bob and he’ll decrypt it with his private key and Alice’s public key.
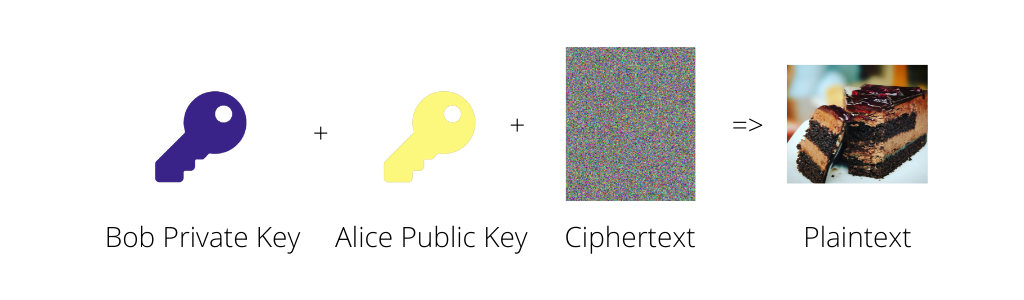
This process works out great because we didn’t have to manually meet somewhere to exchange keys but we have to go through the additional steps of encrypting and decrypting the message twice.
Both?
The downside to public-key encryption is that it’s more computationally expensive than symmetric encryption so a clever solution was devised. We said the challenge with symmetric key encryption is that out of band key exchange and the fact that each group of people who have access to the data in the ciphertext needs to have their own set of keys which makes distribution a challenge.
In a hybrid approach, a symmetric key is generated by Alice. She then encrypts this key using her private key and Bob’s public key. This encrypted key can then be safely sent to Bob where he can decrypt it. Any future message can use the faster symmetric key. This involves a few more steps than each method alone but it has so many benefits.
SSL/TLS is a real-world example of where this is used. Newer implementations even create a one-time-use symmetric key for each connection a user makes so it’s harder to accumulate data over time and break the encryption.
What You Need To Know to Nail a Job Interview
- Symmetric Key encryption uses the same key on both sides
- Asymmetric or public-key encryption uses a public and private key on both sides
- Combining both is used in some methods
Scott Keck-Warren
Scott is the Director of Technology at WeCare Connect where he strives to provide solutions for his customers needs. He's the father of two and can be found most weekends working on projects around the house with his loving partner.
Top Posts
- Working With Soft Deletes in Laravel (By Example)
- Fixing CMake was unable to find a build program corresponding to "Unix Makefiles"
- Upgrading to Laravel 8.x
- Get The Count of the Number of Users in an AD Group
- Multiple Vagrant VMs in One Vagrantfile
- Fixing the "this is larger than GitHub's recommended maximum file size of 50.00 MB" error
- Changing the Directory Vagrant Stores the VMs In
- Accepting Android SDK Licenses From The OSX Command Line
- Fixing the 'Target class [config] does not exist' Error
- Using Rectangle to Manage MacOS Windows